Mentioning Windows BitLocker, I believe many digital enthusiasts are familiar with it.
Simply put, Windows BitLocker is a disk encryption technology developed by Microsoft. It uses various encryption algorithms to convert data stored on a hard drive into a form that cannot be accessed by unauthorized users.
With Windows BitLocker, users can unlock and access the data on the disk only by providing the correct key. Otherwise, the data on the hard drive will remain encrypted and cannot be read or modified.
Looking at Microsoft’s publicity, Windows BitLocker seems very sophisticated and secure, but recently, an embarrassing incident occurred. Third-party security researchers demonstrated a method that could easily crack Microsoft’s Windows BitLocker.
When it comes to cracking Windows BitLocker, some might think it requires a very complex and lengthy process—no, no, not at all. According to the video published by the security researcher, the entire cracking process took less than a minute, only forty-three seconds, which is incredibly easy.
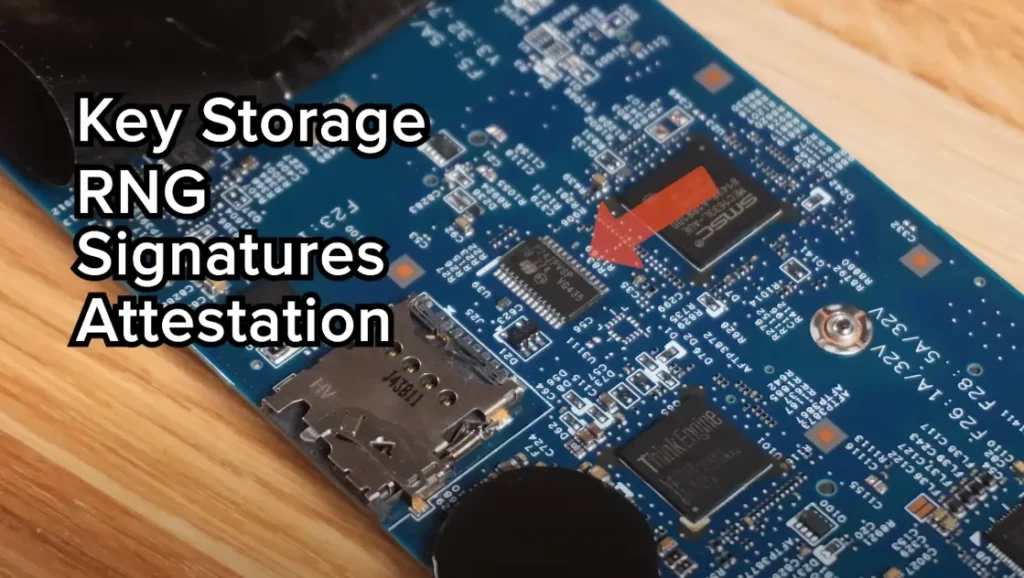
So, how did security personnel crack Windows BitLocker? What are the specific principles and ideas? The approach exploits flaws and vulnerabilities related to TPM. For some computers, the BitLocker function requires the use of an external TPM to store critical information, such as the Platform Configuration Registers and the volume master key.
There is a type of TPM whose keys work by communicating with the CPU via the LPC bus. Unlocking requires sending the key to the CPU, which is the encryption key for the disk encrypted with the Windows BitLocker scheme.

The communication between the CPU and the external TPM at startup is unencrypted, using plaintext communication. This allows the interception and sniffing of data transmitted between them, thereby achieving the purpose of stealing the encryption key.
This is the main principle and idea behind attacking and cracking the Microsoft Windows BitLocker encryption scheme. The key is whether it is possible to successfully capture the data transmitted between the CPU and TPM. To achieve this, some external tools are required.
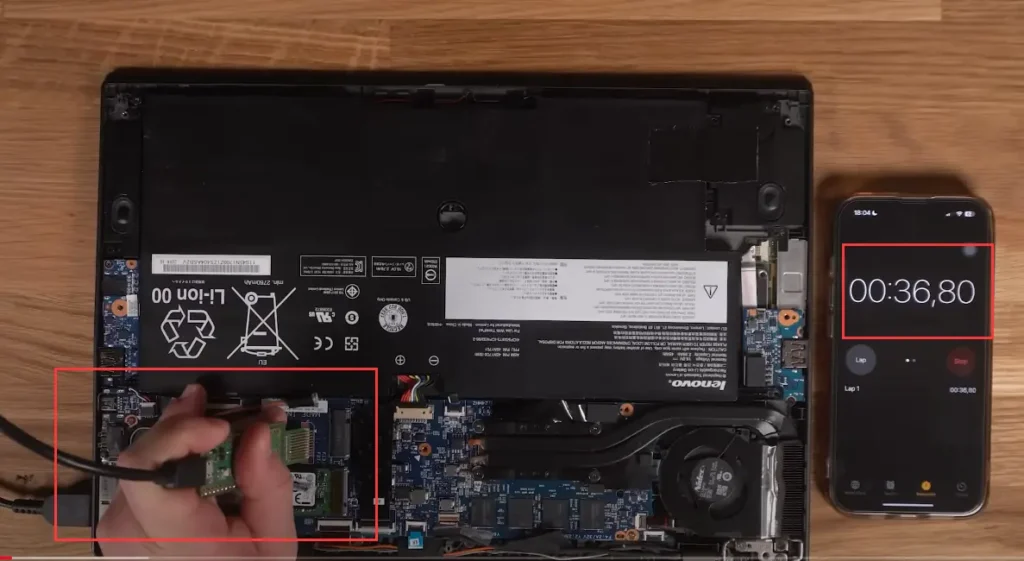
The security researcher used an inexpensive Raspberry Pi Pico device, with a total cost of less than $10. Then, its specific metal contacts were connected to specific points on the computer’s motherboard, specifically a laptop that had been in service for over ten years.
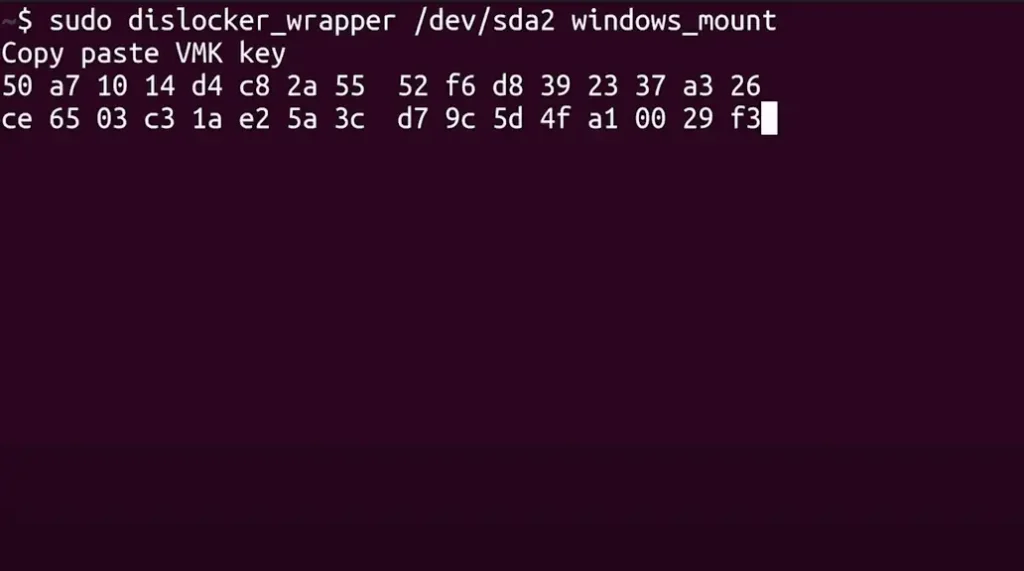
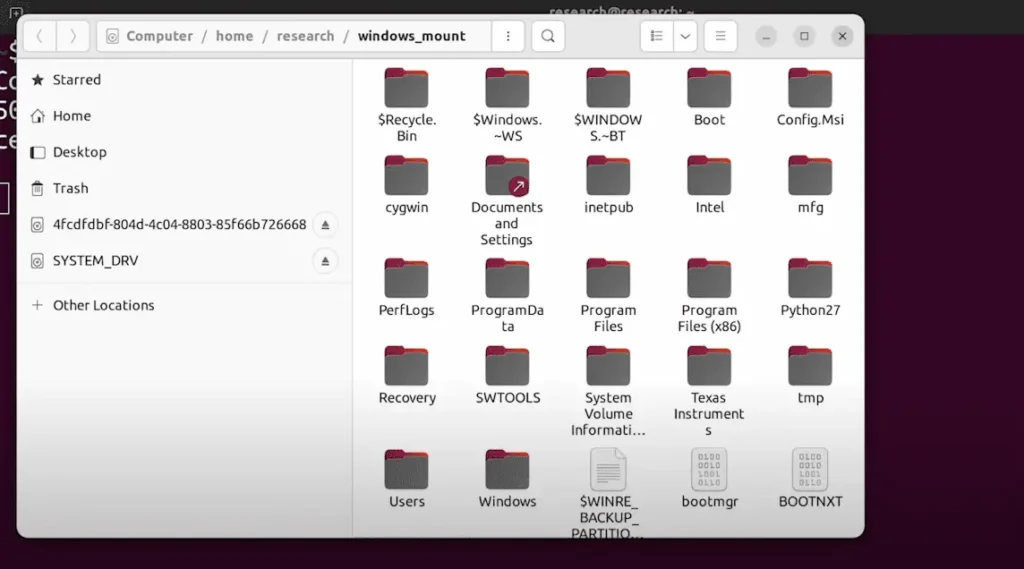
Then, by running a special code on the Raspberry Pi Pico device to read the raw data from the TPM, access to the volume master key stored on the TPM module is granted, easily obtaining the key to access the disk encrypted by Windows BitLocker. Please refer to the three images below.
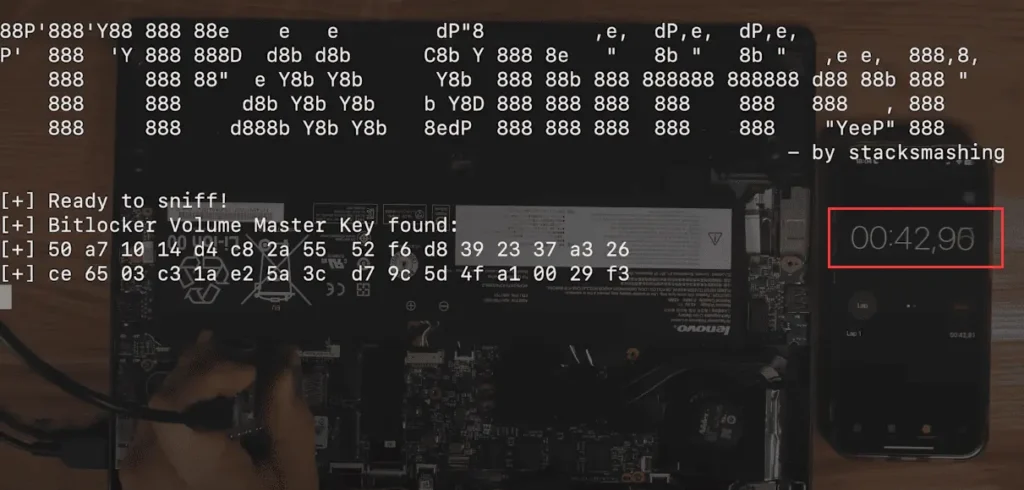
It’s important to clarify that the “entire cracking process taking 43 seconds” does not start after the laptop’s back cover has been removed, the wires connected, and all preparations made. The timing begins with unscrewing and removing the back cover of the laptop, a process that nearly takes 30 seconds. Therefore, the actual cracking process takes less than 20 seconds.
Regarding this cracking case, a few points need to be clarified and explained:
This cracking solution is not a “one-size-fits-all” approach, and its success depends on various factors.
For instance, some Platform Configuration Registers and volume master keys are not stored in external TPM modules but within the CPU itself, making this approach ineffective.
Additionally, there are many implementations and types of TPMs. This method is only applicable to certain types of external standalone TPM modules. Many of the newer processor models in recent years come with built-in soft TPM modules, to which this method does not apply and cannot be cracked.
This attack method requires the attacker to physically access the computer being attacked and cannot be implemented remotely online. For the vast majority of ordinary users, the likelihood of this happening is extremely small, making its academic and research value greater than its practical value, so there is no need for excessive concern. However, for business users who store a large amount of important sensitive data, caution is advised.
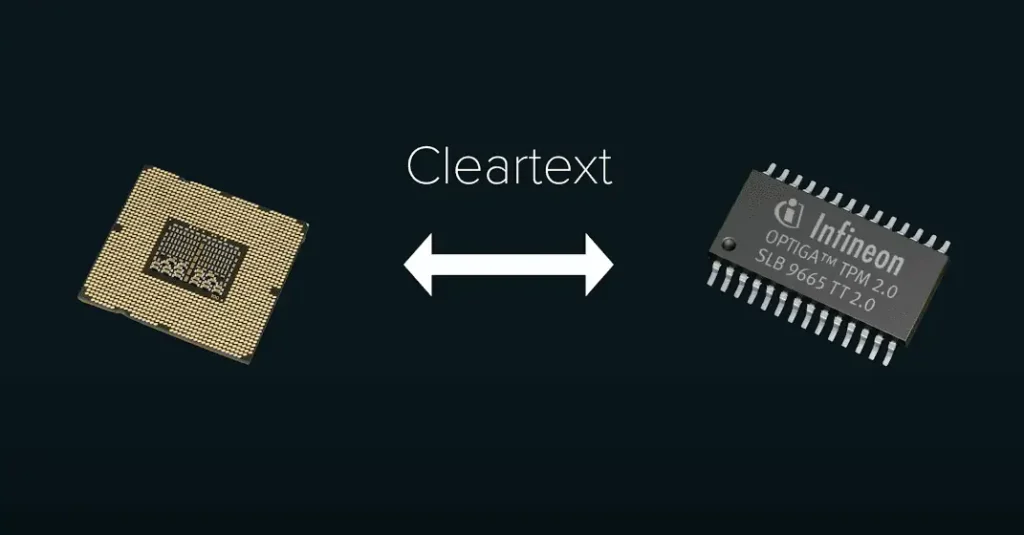
Nonetheless, this case shows that Microsoft’s Windows BitLocker encryption scheme is not as secure as advertised, with plaintext communication between the TPM and CPU being a serious security vulnerability.
However, Microsoft is not solely responsible for this issue; it would be unfair to blame them entirely. TPM manufacturers, processor manufacturers, and operating systems all share responsibility. It requires close cooperation among them to plug this vulnerability, and hopefully, it will be resolved soon.
Related:
- Cracking the Code | Quick Dive into Encryption
- Disable BitLocker Encryption During Windows 11 Installation
- Install Win11 on Old PCs – No TPM 2.0 Needed!

Disclaimer: YUNZE maintains a neutral stance on all original and reposted articles, and the views expressed therein. The articles shared are solely intended for reader learning and exchange. Copyright for articles, images, and other content remains with the original authors. If there is any infringement, please contact us for removal.








