Now a mention of “security”, the majority of digital enthusiasts and friends may first be associated with desktop computers, laptops, smartphones, NAS, and other devices, associated with data leakage, ransom, etc., in fact, compared to these devices, there is a relatively low-profile equipment security is more important.
This is the router, whether it is a home user or enterprise-level user, the router is a variety of endpoints to connect to the network of important transit devices, if the router has a security vulnerability, the consequences will be equally serious, if not more serious.
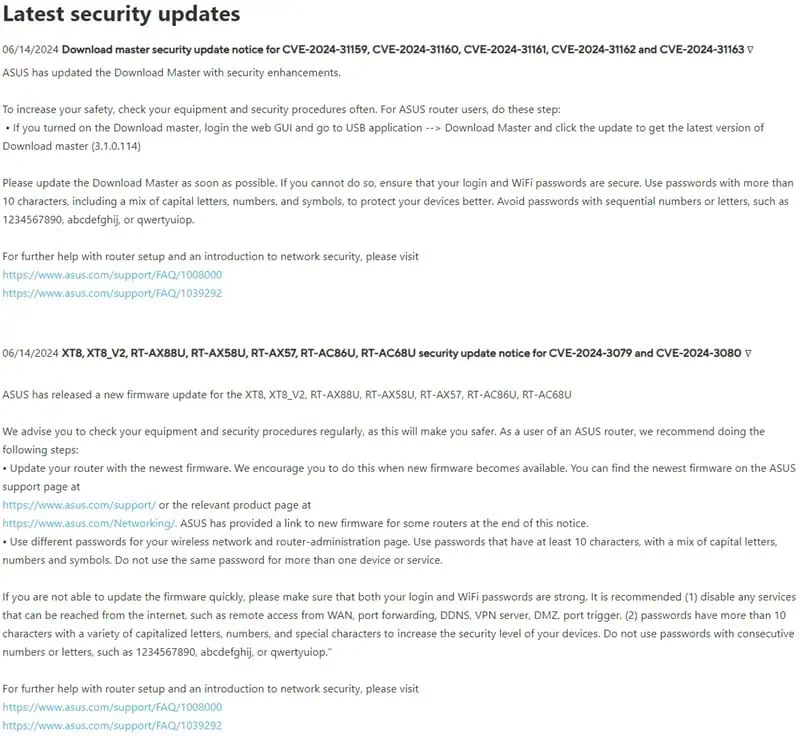
On June 14, renowned hardware manufacturer ASUS released updates for a number of its routers, fixing several security vulnerabilities, including CVE-2024-31159, CVE-2024-31160, CVE-2024-31161, CVE-2024-31162, CVE-2024-31163, CVE-2024-3079, and CVE-2024-3080, see above.
These security vulnerabilities allow hackers to remotely control various models of routers developed and manufactured by the company without authentication.
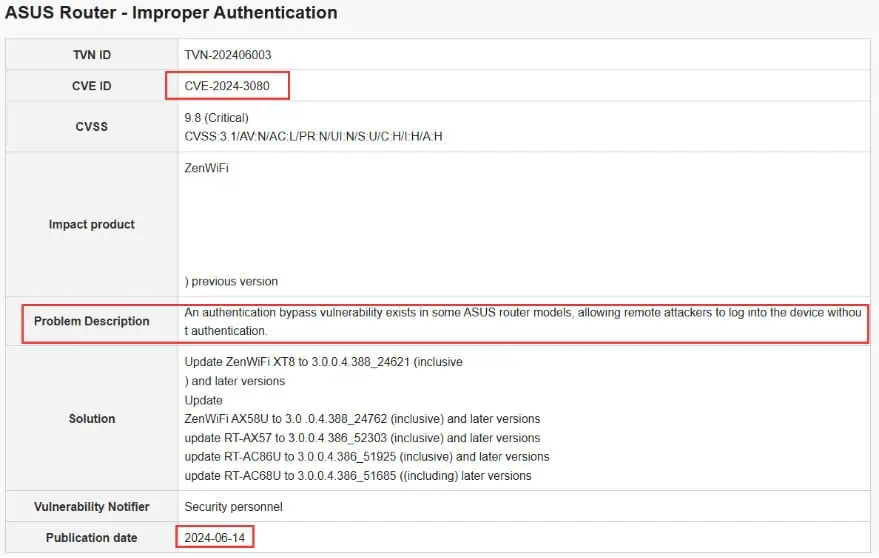
Of these, CVE-2024-3080 is the most serious vulnerability, allowing a remote attacker to log into the device without authentication. With a maximum security severity rating of 10, the vulnerability scores 9.8 out of 10, making it a high-risk vulnerability, see the chart above.
ASUS processor models with this vulnerability include XT8 and XT8 V2, RT-AX88U, RT-AX58U, RT-AX57, RT-AC86U, and RT-AC68U.
CVE-2024-3079 is a buffer overflow vulnerability that hackers can exploit to remotely execute commands on affected routers.
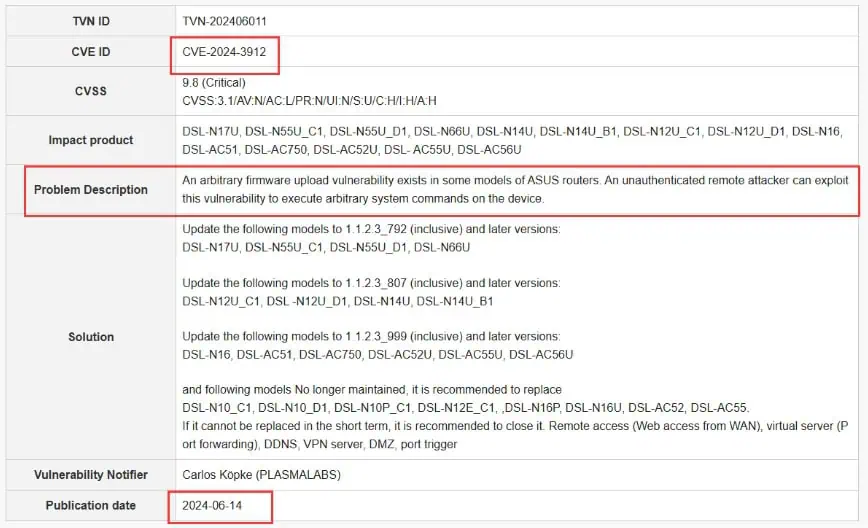
The CVE-2024-3912 vulnerability is very similar to CVE-2024-3080, allowing a hacker to remotely execute commands without the need for user authentication, and the vulnerability also carries a severity rating of 9.8, see the chart above.
Processor models with this vulnerability include:
DSL-N12U_C1, DSL-N12U D1, DSL-N14U, DSL-N14U_B1, DSL-N16, DSL-N17U, DSL-N55U_C1, DSL-N55U D1, DSL-N66U, DSL-AC51/DSL-AC750, DSL-AC52U, DSL- AC55U, and DSL-AC56U.

In addition, the CVE-2024-3912 vulnerability is also present in some older models of ASUS routers, but these devices have passed their lifecycle and ASUS will not release a fix pudding for these models, and users are advised to simply replace them, which include:
DSL-N10_C1, DSL-N10_D1, DSL-N10P_C1, DSL-N12E_C1, DSL-N16P, DSL-N16U, DSL-AC52 and DSL-AC55.
If you are an ASUS router user, then you should immediately check and verify to make sure that your product belongs to one of the above-affected models, and if so, you should download and update the firmware immediately to ensure that your device is safe.

Disclaimer: This article is created by the original author. The content of the article represents their personal opinions. Our reposting is for sharing and discussion purposes only and does not imply our endorsement or agreement. If you have any objections, please get in touch with us through the provided channels.








