Encryption algorithms are technologies that must be used in every software project nowadays. The application scenarios include user logins, transactions, information communication, OAuth, and more. Different application scenarios may also require the use of different signature encryption algorithms. This article will briefly introduce several common encryption algorithms.
01
What is an Encryption Algorithm?
An encryption algorithm is a cryptographic technique that transforms information into ciphertext, ensuring the privacy of the data’s owner while enabling anonymous data sharing. Encryption algorithms achieve the following:
- Data confidentiality: Prevents theft or leakage of user data.
- Data integrity: Protects data transmitted by users from being tampered with.
- Mutual identity verification of communicating parties: Ensures the legitimacy of data sources.
Common encryption algorithms are divided into irreversible and reversible algorithms. Reversible algorithms are further categorized into symmetric and asymmetric encryption algorithms, as shown in Figure 1 of the overall encryption algorithm classification.

02
Irreversible Algorithms
Irreversible algorithms ensure that the encrypted data cannot be reversed to its original form. One such type of algorithm is a hashing algorithm.
Hashing algorithms refer to the process where plaintext data is transformed into a fixed-length hash value, irrespective of the length of the plaintext. The algorithm process is depicted in Figure 2. Several common implementations of hashing algorithms exist, including MD5, SHA-1, SHA-224, SHA-256, and more. Hashing algorithms do not require a key, although some other irreversible algorithms, like HMAC, do.

① MD5 (Message-Digest Algorithm 5): MD5 can transform data of any length into a fixed-length hash value. MD5’s output length is 128 bits, typically represented as 32 hexadecimal characters. While MD5 boasts advantages such as speed and fixed output length, it has a significant drawback – it is insecure. MD5 has been compromised, and its limited output length makes it vulnerable to attacks like brute force or rainbow table attacks, allowing attackers to find identical hash values to the original data. Although salting, and adding a variable string to the plaintext, can mitigate this, it’s advisable to replace MD5 with more secure SHA series algorithms.
② SHA (Secure Hash Algorithm) Series: The SHA series comprises a set of cryptographic hash functions designed by the U.S. National Security Agency (NSA) in 1993. It includes SHA-1, SHA-2, and SHA-3 versions. SHA-1 is flawed and no longer recommended. SHA-2 encompasses SHA-224, SHA-256, SHA-384, and SHA-512, mapping data of any length to hash values of 224, 256, 384, and 512 bits, respectively.
Comparatively, SHA-2 is stronger than MD5 for two main reasons:
- Longer hash values: For instance, SHA-256 generates a 256-bit hash value, while MD5 produces a 128-bit one, making brute force or rainbow table attacks more challenging.
- Enhanced collision resistance: SHA algorithms employ more intricate computational processes and additional rounds, making it harder for attackers to find collisions through precomputation or coincidence.
03
Reversible Algorithms
Reversible algorithms are divided into two categories: symmetric encryption and asymmetric encryption.
① Symmetric Encryption
Symmetric encryption uses the same key for both encryption and decryption processes, making the security of the key crucial. If the key is compromised, an attacker can easily decrypt the encrypted data.
The principle of symmetric encryption, as shown in Figure 3, involves two communicating parties agreeing on a shared encryption and decryption algorithm, along with a unique salt (a random value) to identify the data. Before sending data, it is encrypted using the encryption algorithm and salt, resulting in ciphertext. The recipient then uses the decryption algorithm along with the salt to decrypt the ciphertext back into plaintext.
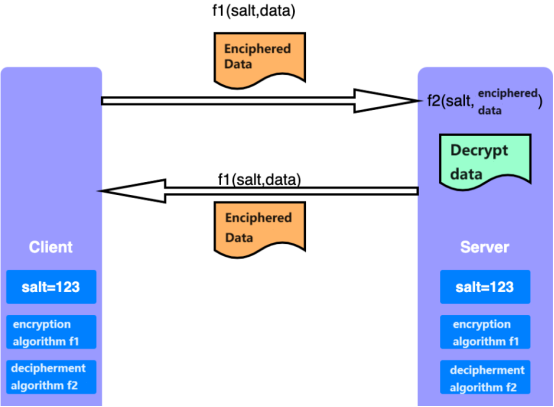
Common symmetric encryption algorithms include DES (Data Encryption Standard), 3DES (Triple Data Encryption Standard), and AES (Advanced Encryption Standard). Among these, AES is widely used and known for its high security and encryption efficiency.
- AES (Advanced Encryption Standard): AES is a widely employed symmetric encryption algorithm in data encryption and protection. It uses key lengths of 128 bits, 192 bits, or 256 bits, which are longer and more secure than DES. AES boasts a larger key space, enhanced security, and resistance to brute force attacks. However, the longer key lengths require more storage.
- DES (Data Encryption Standard): DES is one of the earliest widely used symmetric encryption algorithms. It uses a 56-bit key for data encryption, incorporating operations like permutation, substitution, and XOR. While DES is relatively fast, it is not the optimal choice for security due to its short key length, making it vulnerable to brute force and differential attacks. It is generally recommended to use more secure symmetric encryption algorithms like 3DES or AES.
② Asymmetric Encryption
Asymmetric encryption requires two distinct keys: a public key and a private key. These keys are dissimilar but complementary. When data is encrypted with one key, only the other key can decrypt it. This approach has the following characteristics:
- Data encrypted with the public key can only be decrypted with the private key; the public key cannot decrypt it.
- Data encrypted with the private key can only be decrypted with the public key; the private key cannot decrypt it.
- The server holds both the public and private keys and keeps the private key secret.
- The server shares its public key with those it wishes to communicate with.
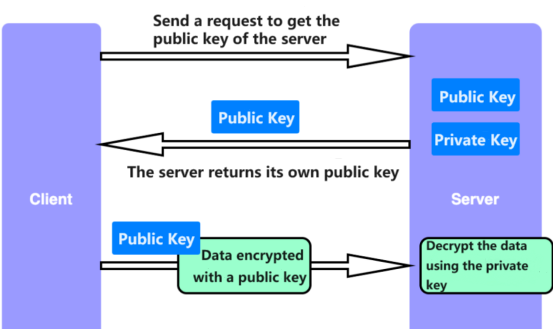
RSA (Rivest–Shamir–Adleman) is currently one of the most widely used asymmetric encryption algorithms. Its strengths lie in high security, the ability to publicly share the public key, and the necessity to keep the private key secure. RSA is used for various applications, including digital signatures and key exchange. However, it has the drawback of slower encryption and decryption, with longer key lengths increasing processing time and storage requirements. Short key lengths are vulnerable to brute force attacks, while long key lengths incur greater computational and storage costs.
Related:
- BitLocker Security Questioned: Cracked in Just 43 Seconds!
- Apple Resolves Butterfly Keyboard Issue: Up to $395 Payout

Disclaimer: This article is created by the original author. The content of the article represents their personal opinions. Our reposting is for sharing and discussion purposes only and does not imply our endorsement or agreement. If you have any objections, please contact us through the provided channels.








